Steps to set Auth0 as an OIDC identity provider
1
Navigate to the Applications view within your Auth0 account.
2
Either use the default application or create a new application by clicking on the Create Application button.
3
A dialog will open, give the app a name, select the type of application and then click on the Create button.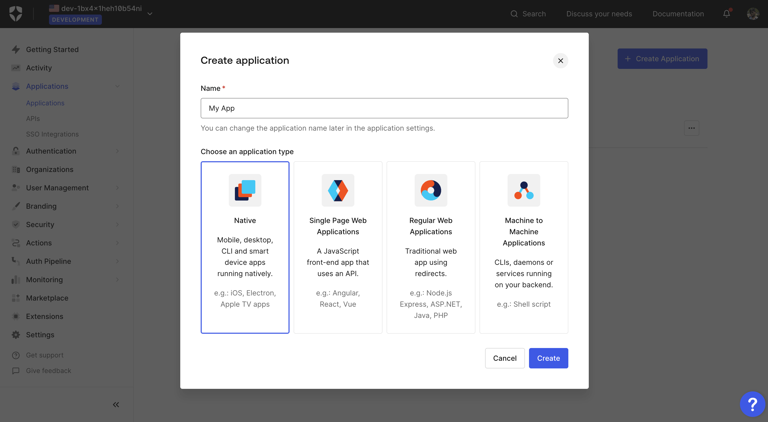

4
Once the app is created, navigate to the Setting tab. Now copy the Domain, Client ID and Client Secret.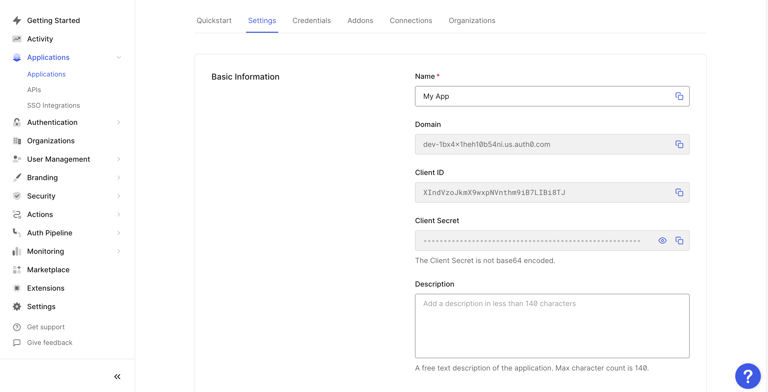

5
Navigate to the settings page on Cosmo.
6
- Click on Connect.
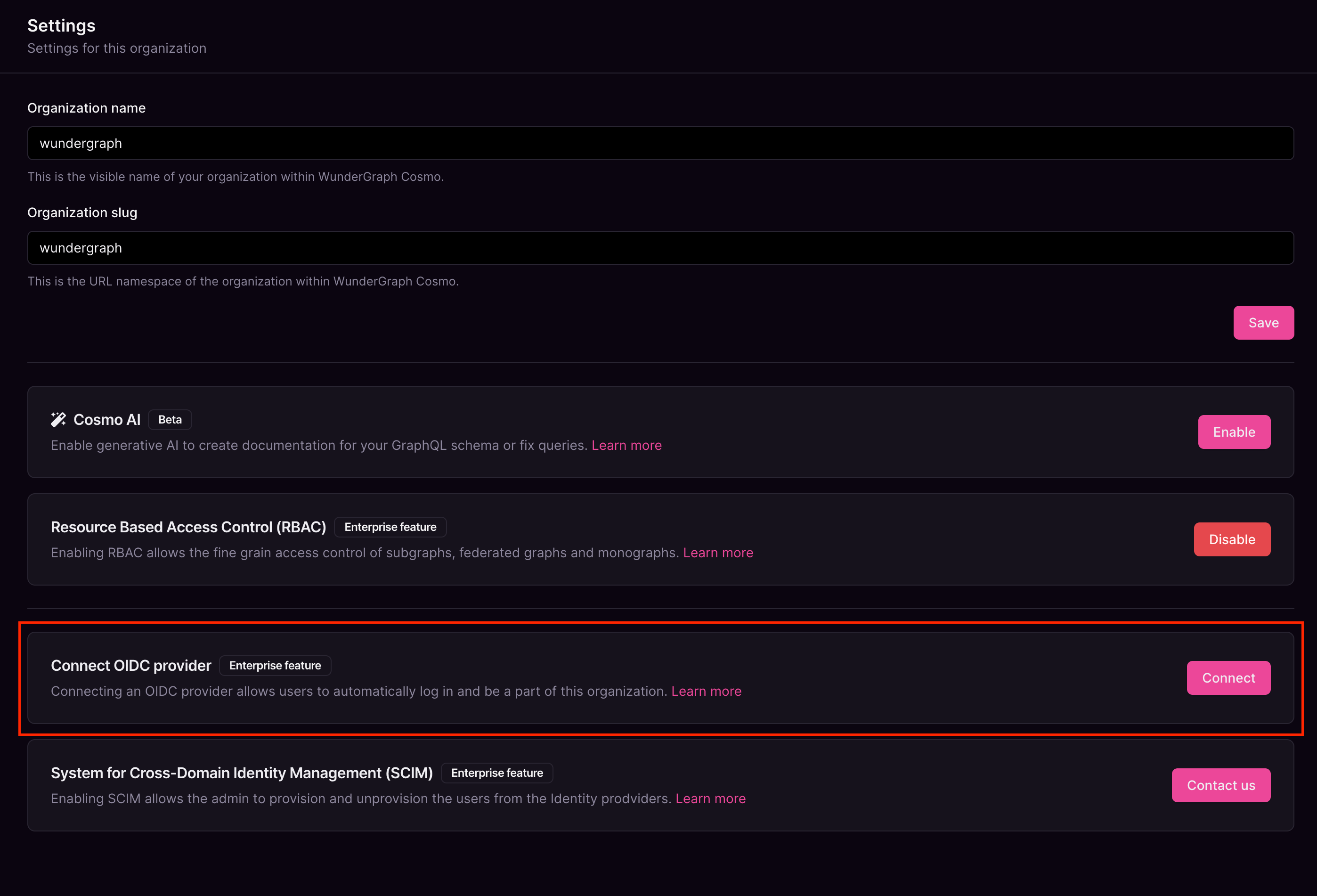
7
Give the connection a name, the Discovery Endpoint will be 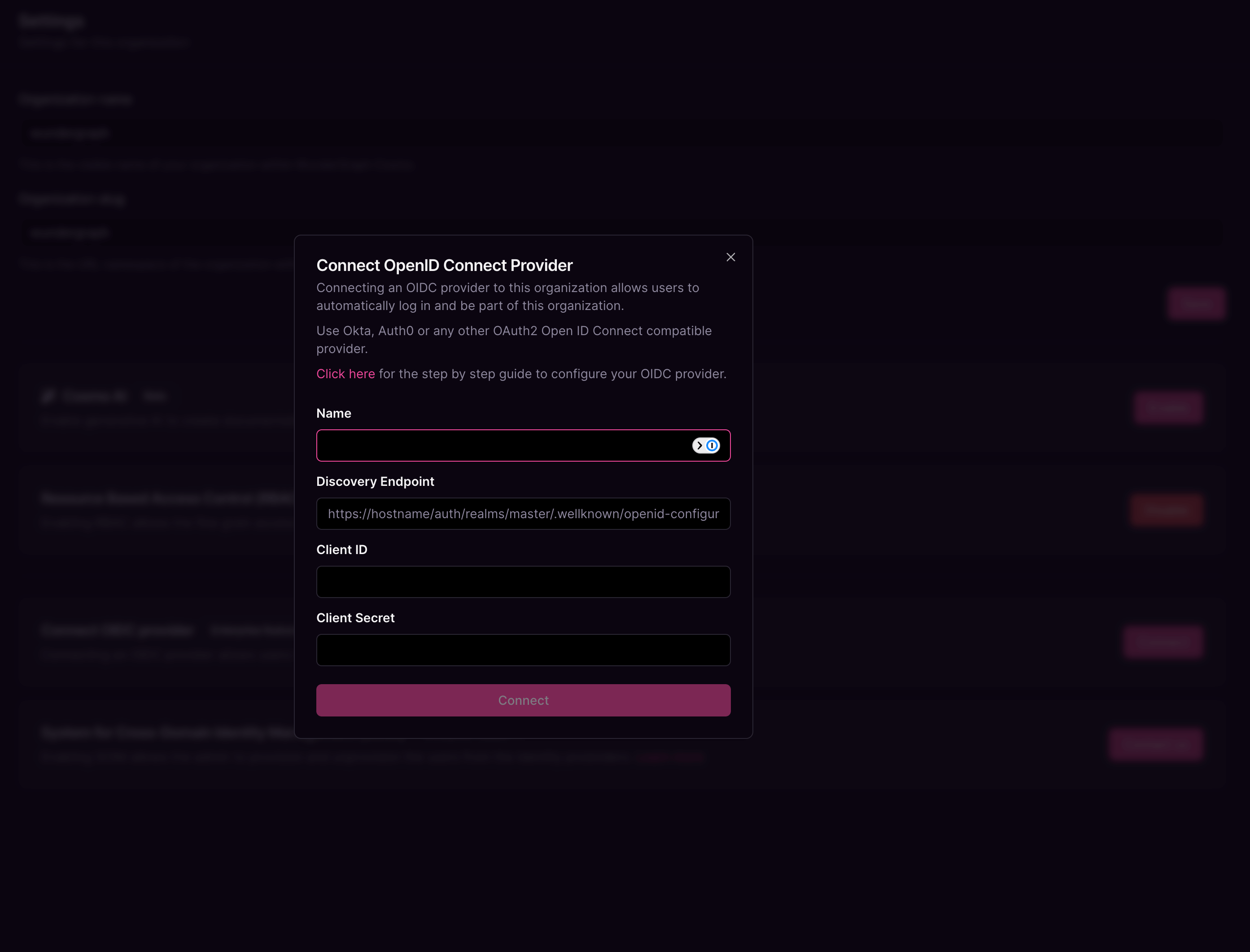
https://YOUR_AUTH0_DOMAIN/.well-known/openid-configuration , and paste the Client ID and Client secretcopied before into the Client ID and Client Secret fields respectively, and then click on Connect.
8
Configure the mapping between the roles in Cosmo and the user roles in Auth0. The field Group in the provider can be populated with the name of the role or a regex to match the user roles. Once all the mappers are configured, click on Save.

9
Copy the sign-in and sign-out redirect URIs displayed in the dialog.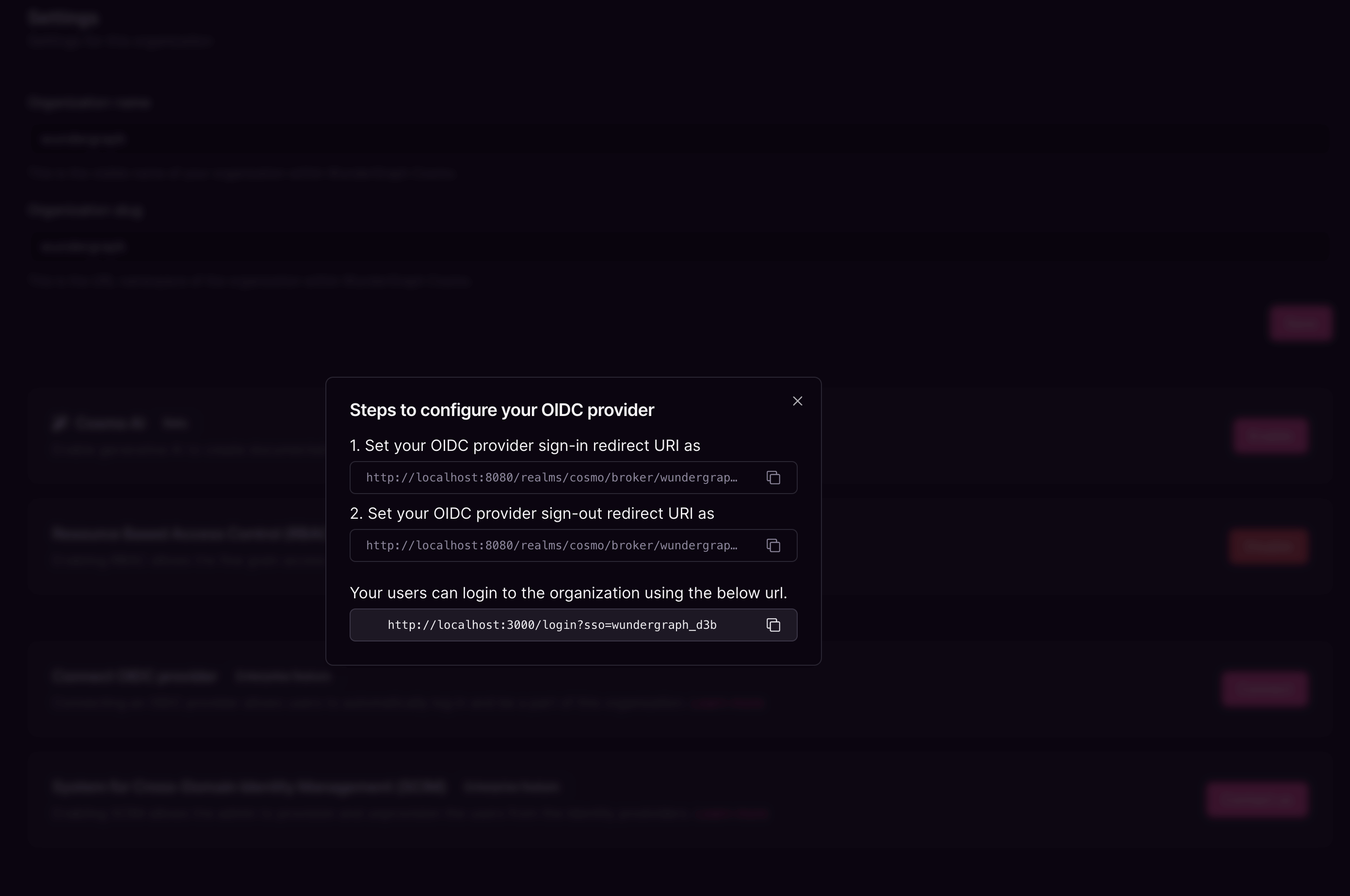

10
Navigate back to the settings tab of the application created on Auth0 and populate the Allowed Callback URLs and Allowed Logout URLs redirect URIs with the above-copied sign-in and sign-out URLs respectively. Click on Save Changes.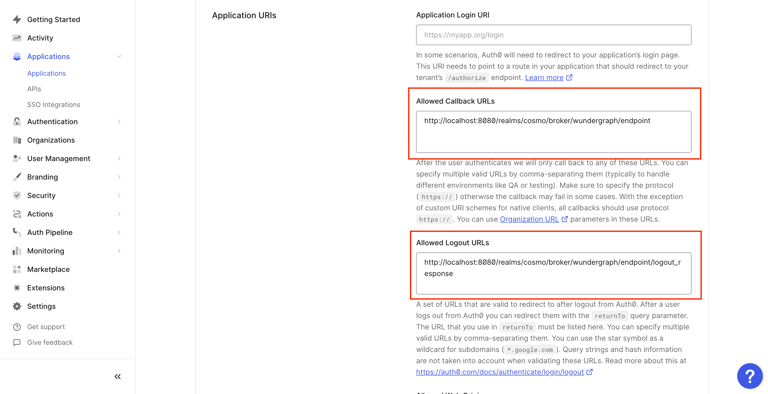

11
Now navigate to Actions -> Library, and then click on the Build Custombutton.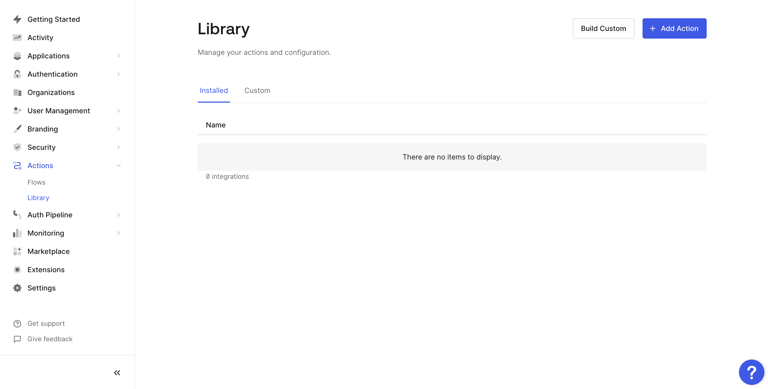

12
Give the action a name, select Login/Post Login as the Trigger and Node 18 as the Runtime and then click the Createbutton.
13
Copy the below code and paste it into the editor shown, then click the Deploy button.
14
Now navigate to Actions -> Flows, and then click on the Loginflow.
15
Navigate to the Custom tab on the right side of the page. Now drag the action and place it between Start and Complete as shown below, and then click on Apply.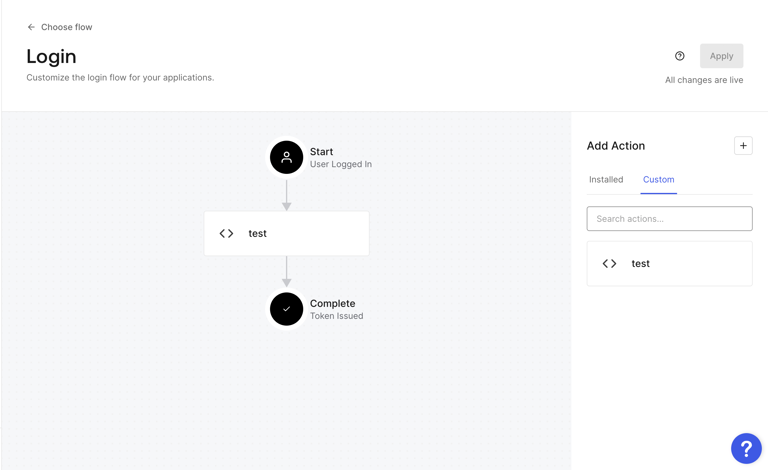

16
Now you can assign users/groups to the application, and those users will be able to log into Cosmo using the URL provided on setting up the provider.