Steps to set Okta as an OIDC identity provider
1
Navigate to the Applications view within your Okta Administrator Dashboard.
2
Click on Create App Integration.
3
A dialog appears, select OIDC - OpenID Connect as the sign-in method.
4
For the application type, select Web Application and click on Next.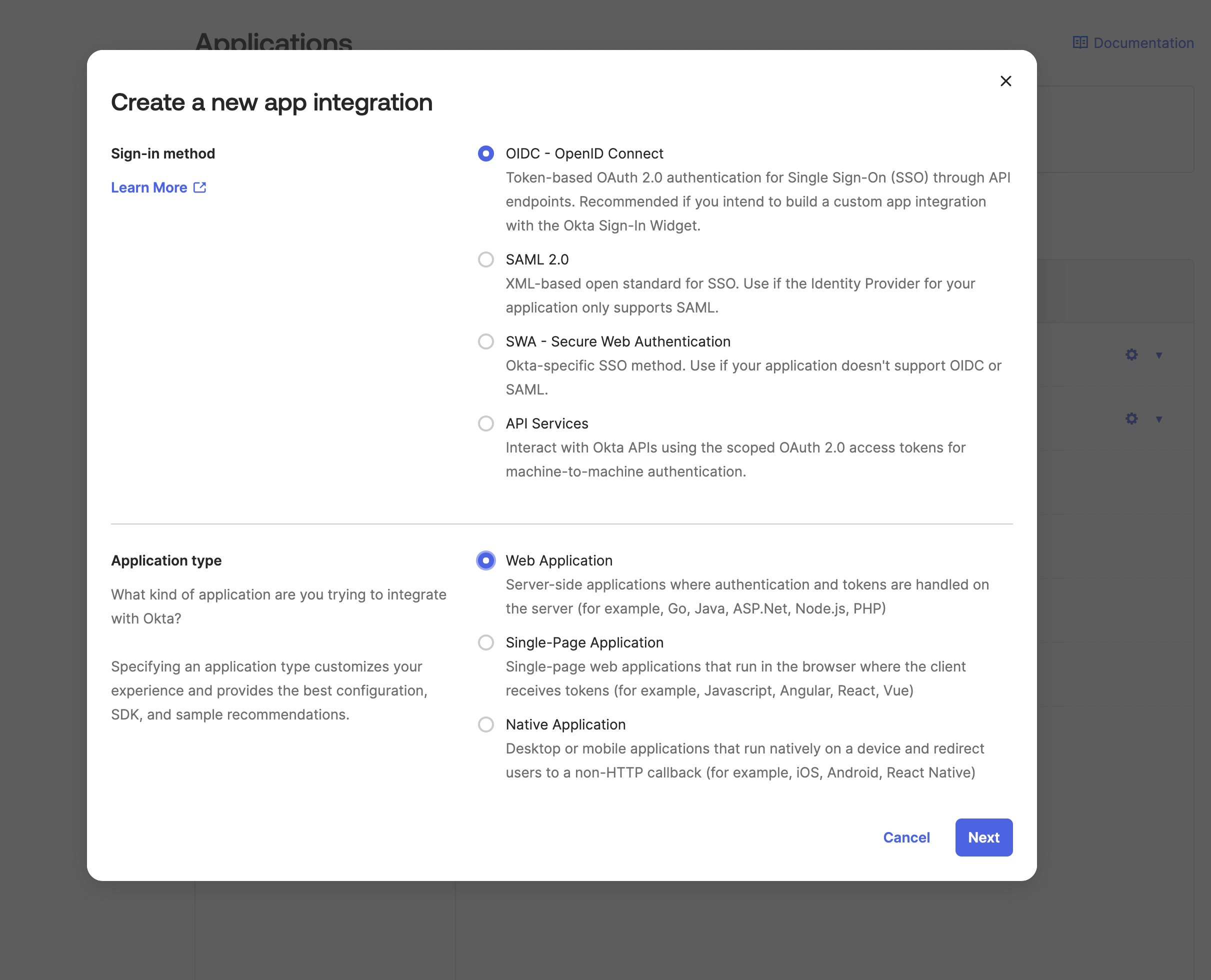

5
Now give the app a name.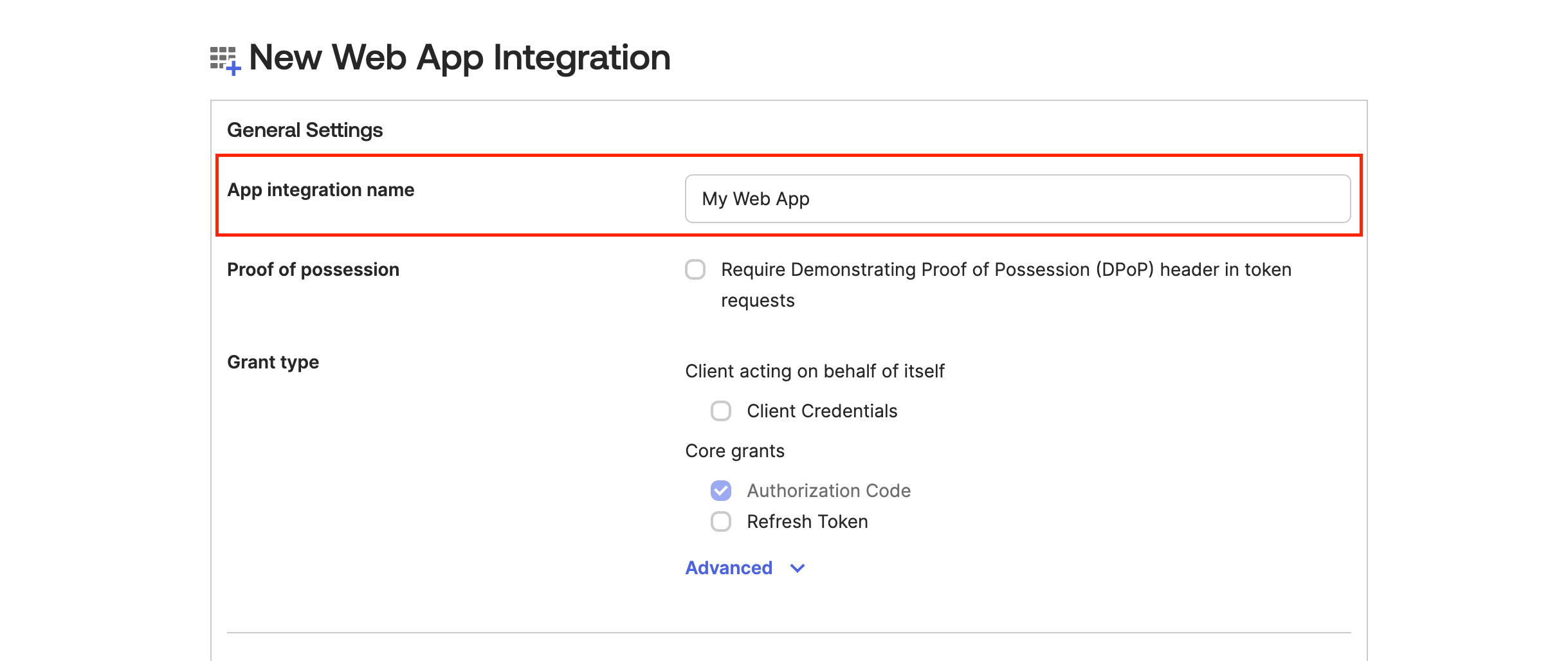

6
For Grant Type, keep the defaults.
7
Scroll down to the Assignments section and select one of the options based on your choice and then click on Save.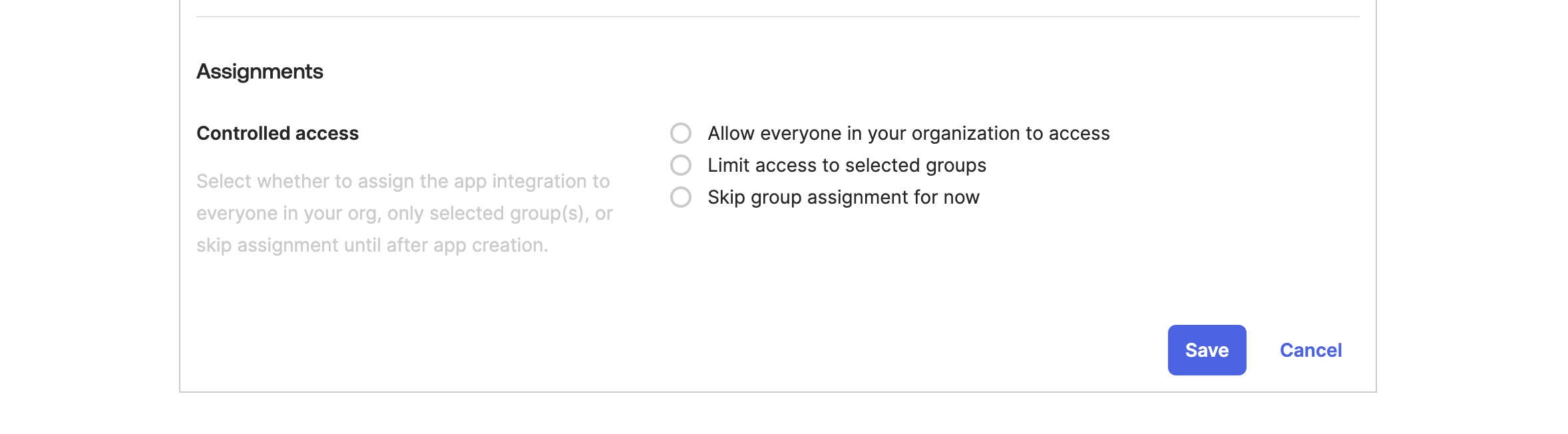

8
Copy the Client ID and Client Secret.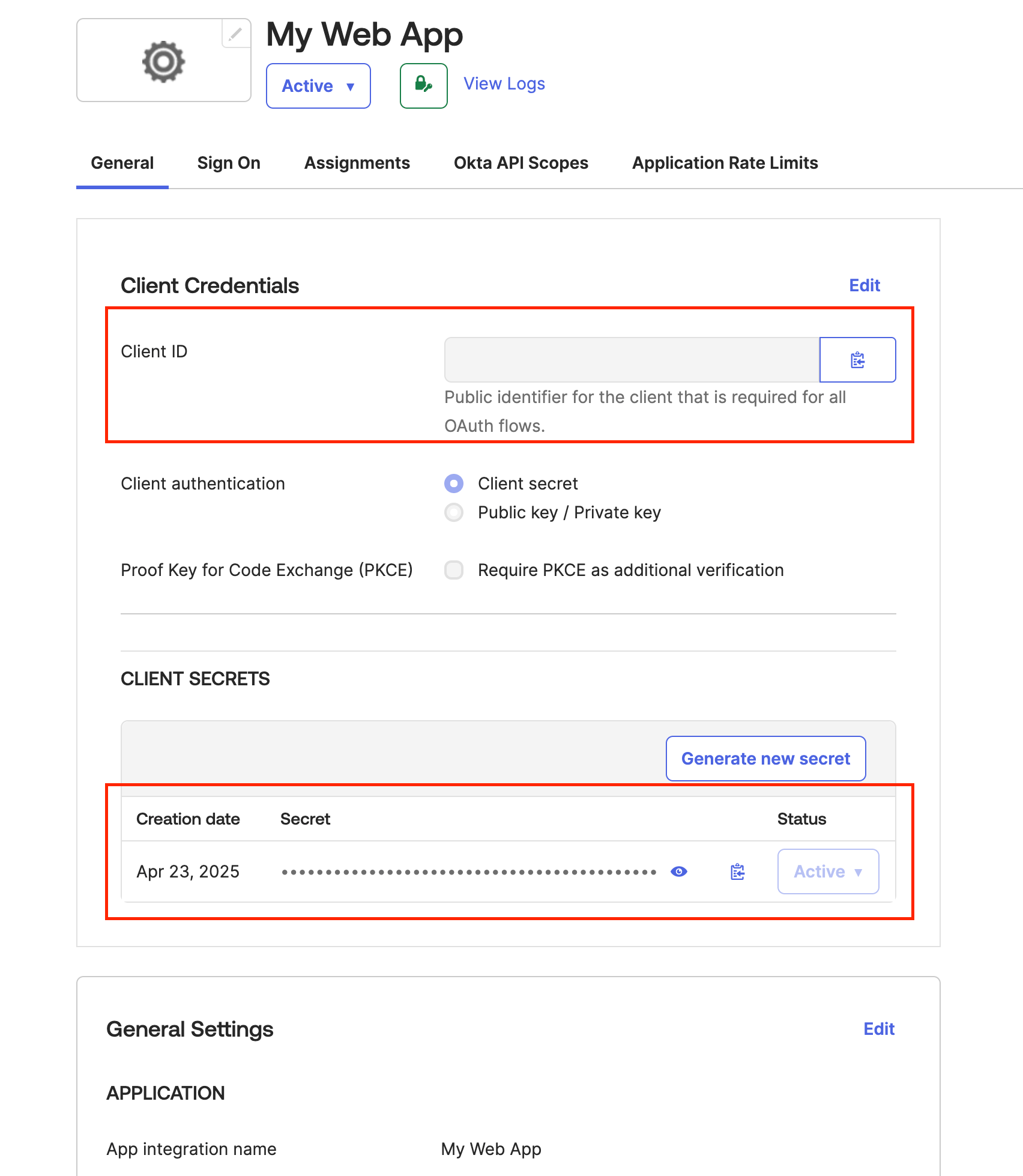

9
Navigate to Security -> API.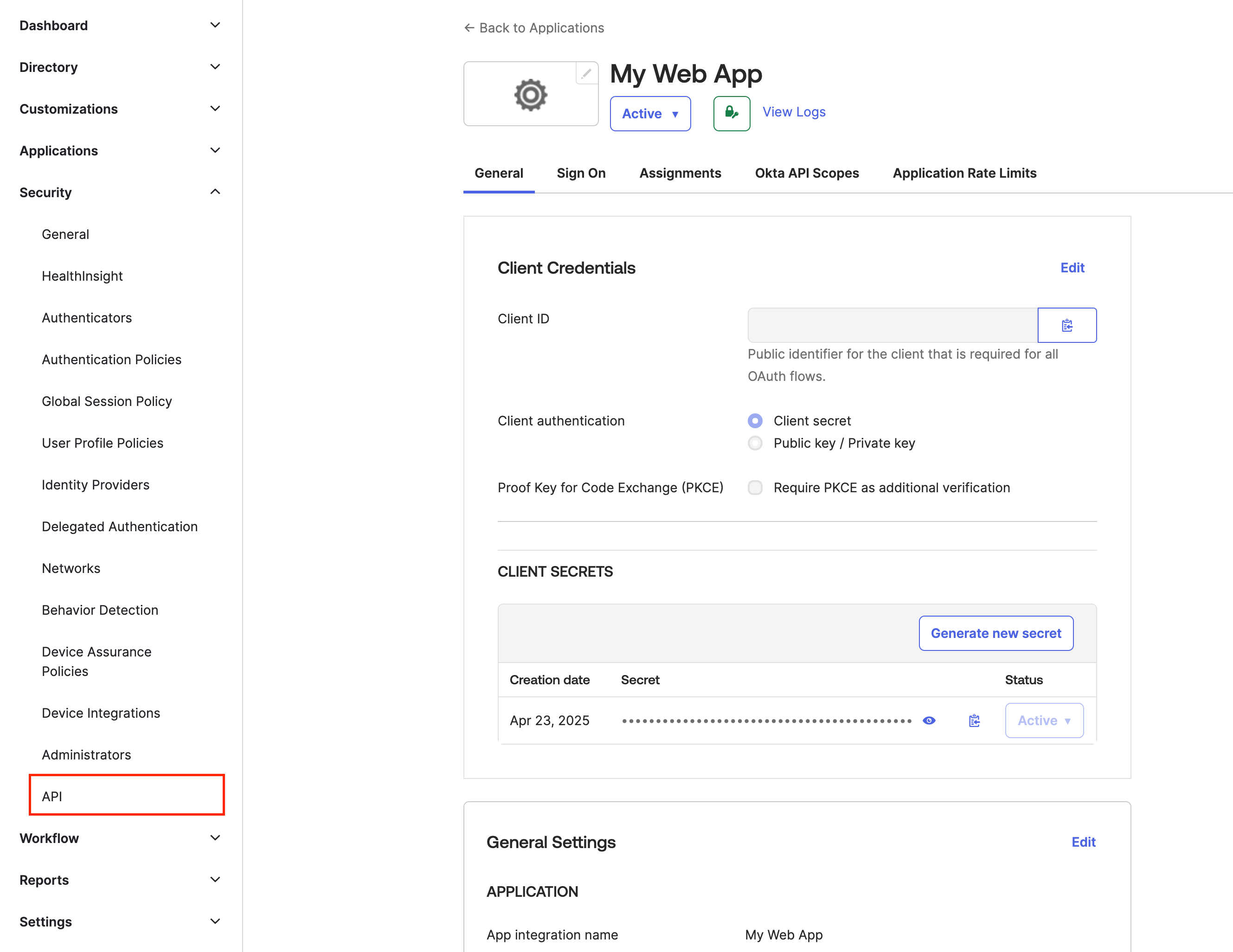

10
Select the default authorization server.
11
Copy the Metadata URI.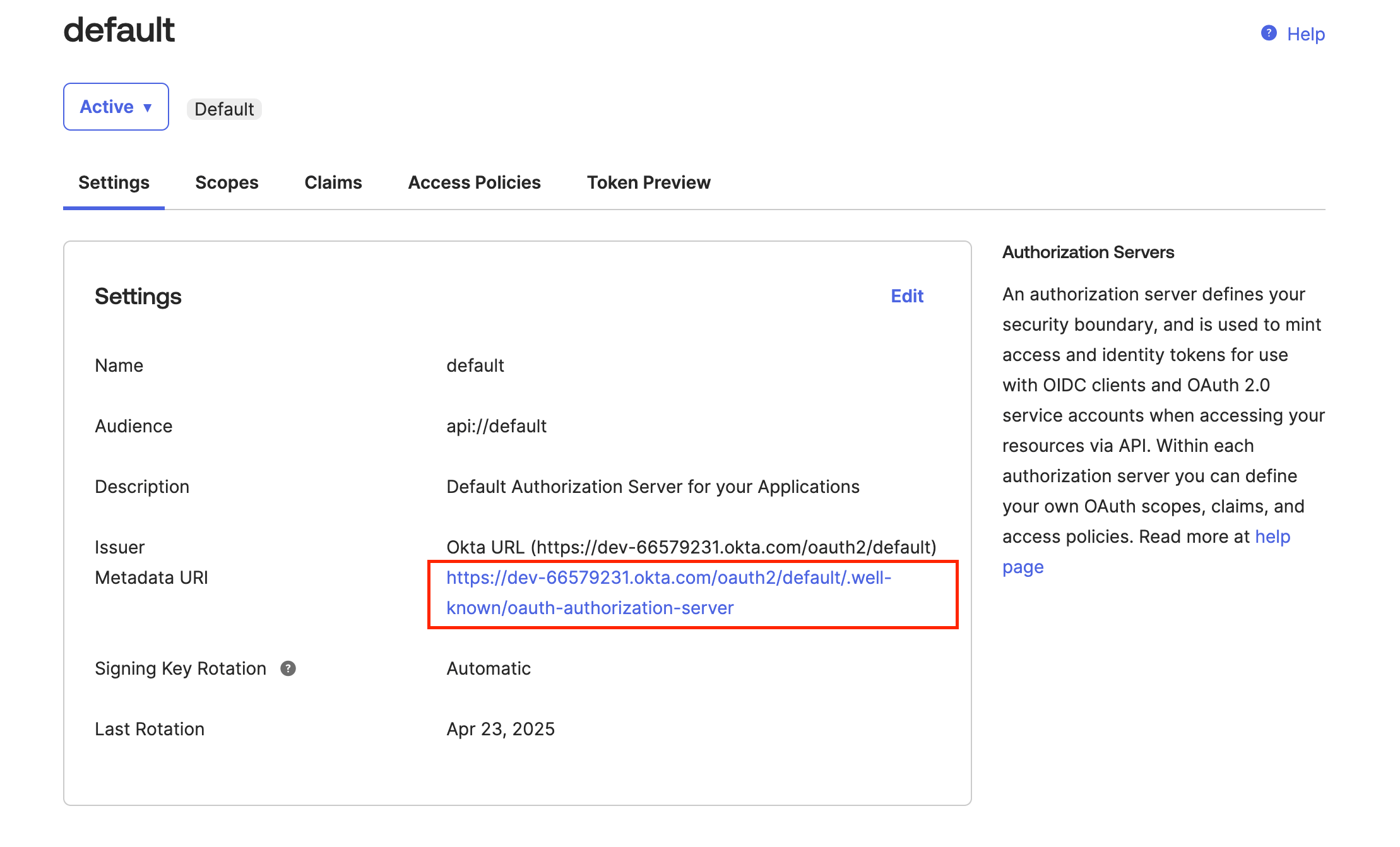

12
Navigate to the settings page on Cosmo.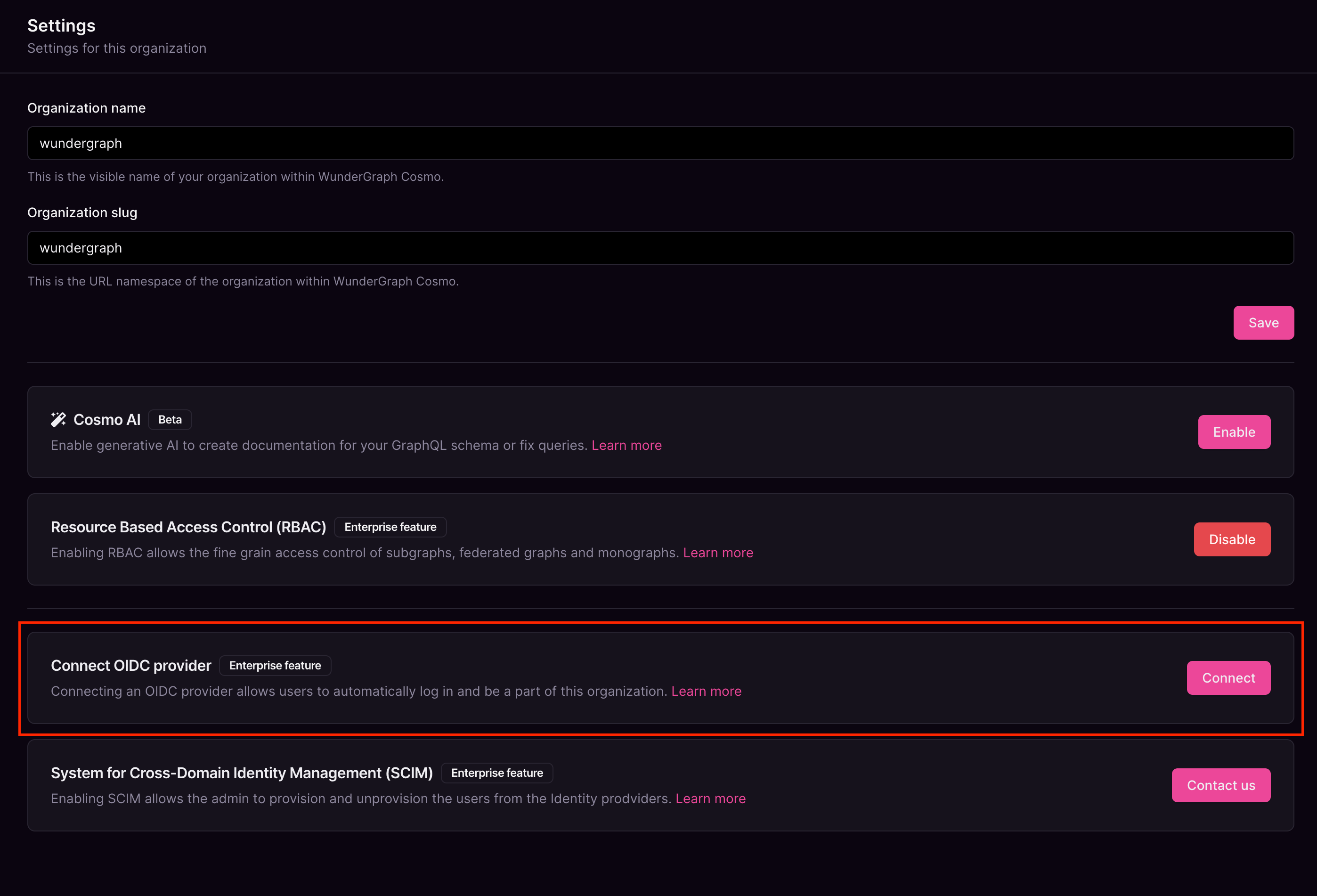

13
Give the connection a name, paste the Metadata URI copied before, into the Discovery Endpoint,and paste the Client ID and Client secret copied before into the Client ID and Client Secret fields respectively,and then click on Connect.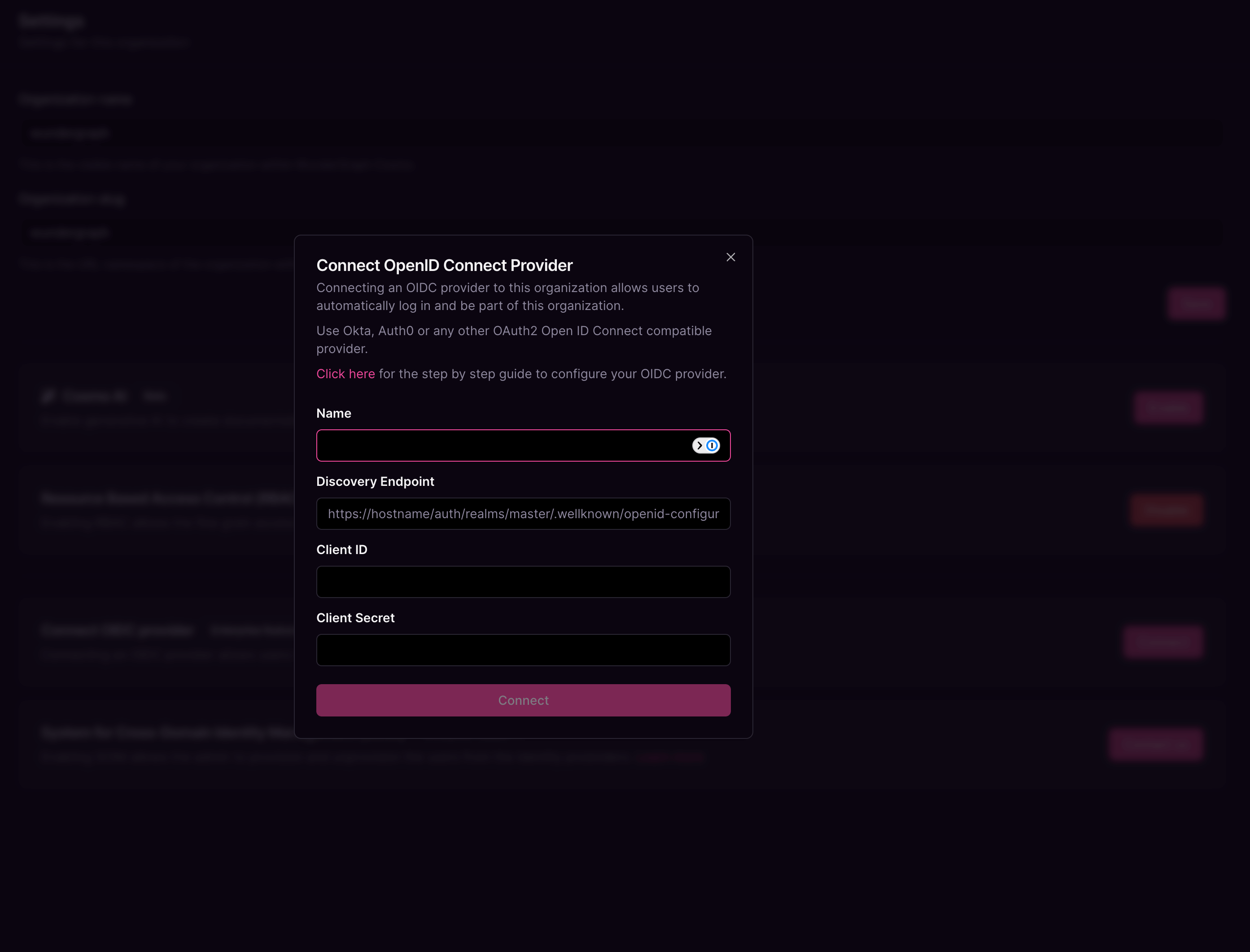

14
Configure the mapping between the roles in Cosmo and the user groups in Okta. The field Group in the provider can be populated with the name of the group or a regex to match the user groups. Once all the mappers are configured, click on Save.

15
Copy the sign-in and sign-out redirect URIs displayed in the dialog.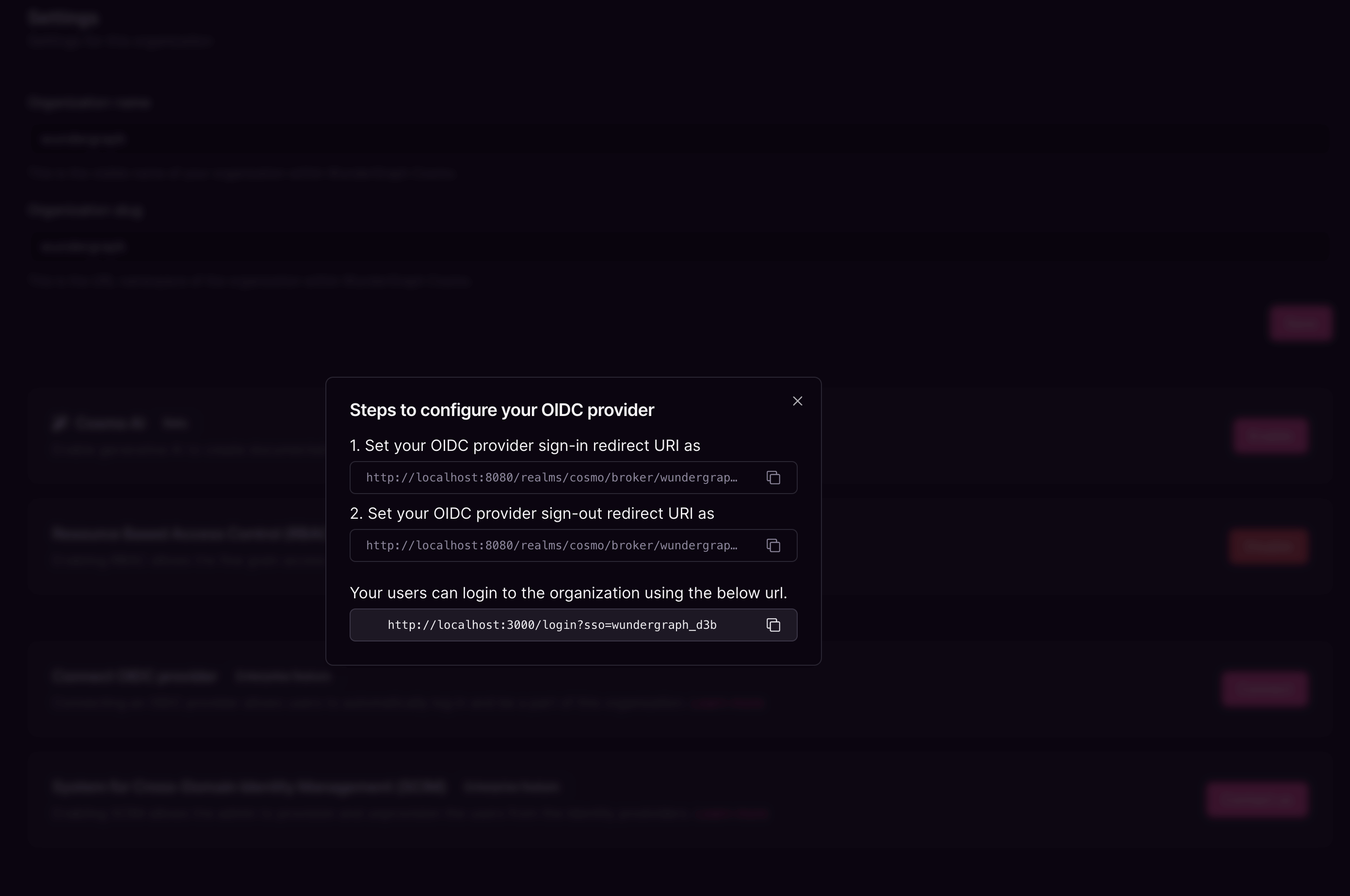

16
Navigate back to the application created on Okta and populate the Sign-in and Sign-out redirect URIs with the above-copied values. Click on Save.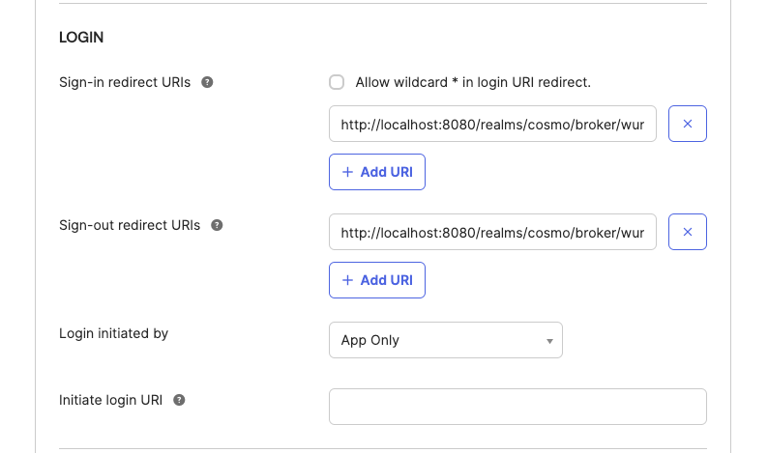

17
Navigate to Security-> API, and click on the default auth server. Navigate to the claims tab and then click on Add Claim.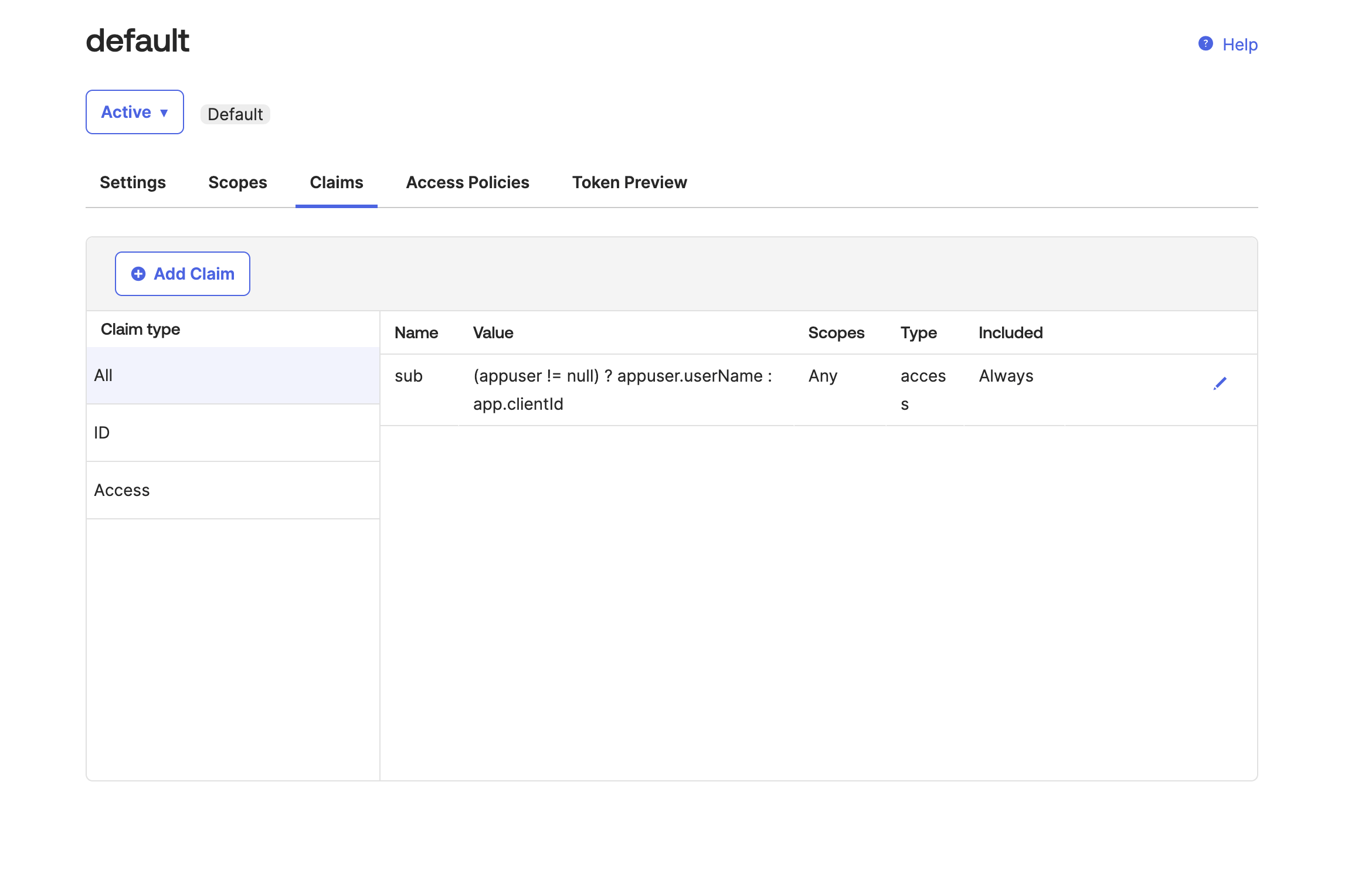

18
Name the claim “ssoGroups”, and include it in the ID Token, for the value type select Groups, and for the filter select Matches regex and populate the field with ”.*”.Click on Create.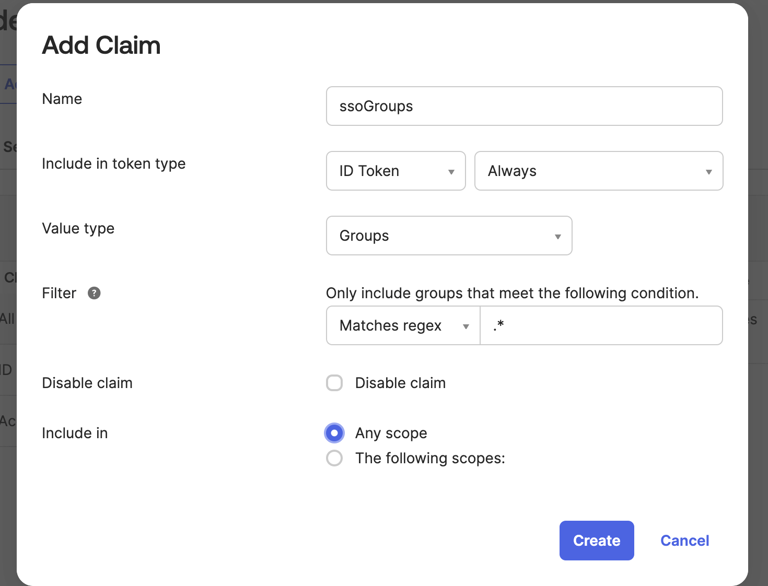

19
Now you can assign users/groups to the application, and those users will be able to log into Cosmo using the URL provided on setting up the provider.
Please make sure that the users added to the application have a username.